The Cicada 3301 Internet Mystery
The recruitment puzzle (?) that spilled from 4chan onto payphones, PGP, Tor, music files, and runic pages — then vanished, leaving a book no one can fully read.
⏱ Timeline callout — January 2012
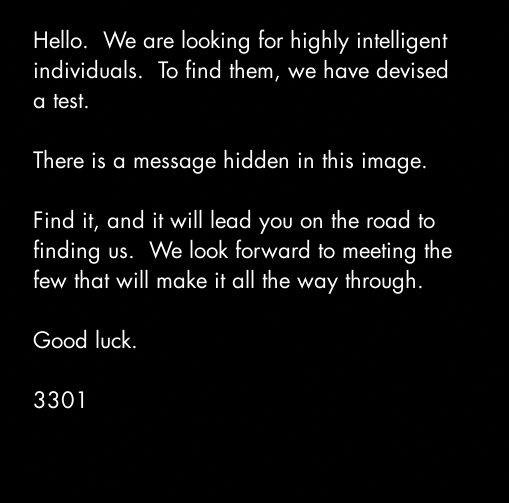
A plain black JPEG lands on 4chan: “We are looking for highly intelligent individuals…” The image is a door disguised as a wall. Behind it: PGP signatures, a phone line, a string of primes, a website, and—days later—QR posters blooming on power poles from Warsaw to Honolulu.
You don’t expect a life to tilt because of a JPG. Yet Cicada 3301 didn’t present itself like a marketing campaign or a prank; it felt monkish. The typography was severe. The instructions were polite. And the test did something rare on the internet: it rewarded patience and punished showing off.
Running the file through OutGuess, a classic steganography tool, peeled back a PGP‑signed message: from now on, the group’s “real” communications would be signed by a single key — ID: 7A35090F — available on public keyservers. That one sentence quietly set the rules for the next five years.
🏷 Only messages signed by key 7A35090F are real.
A simple book cipher and a substitution later, solvers found a US phone number with a calm, lo‑fi voice. The recording congratulated callers, then dropped three primes — 503, 509, 3301 — the last a number that reappears like a sigil throughout the story. Multiply those numbers, tack on “.com,” and the trail shifted from screen to street: GPS coordinates.
In city after city—Seoul, Paris, Seattle, Miami, Warsaw—seekers photographed QR posters taped to poles, scanned them, and plunged into Tor. The instruction there was not “go viral.” It was: don’t collaborate publicly. Only the first finishers moving quietly would be invited further.
Inside the quiet room
What happens if you make it “in”? We have a few good windows.
Joel Eriksson, a Swedish infosec researcher, told reporters the 2012 endpoint wasn’t a ta‑da; it was a small, PGP‑gated forum with tasks aligned to privacy, cryptography, and censorship‑resistant tools.
Marcus Wanner, profiled elsewhere and later interviewed on camera, describes something similar — an expectation of craft and discretion rather than hype. Both accounts agree on the vibe: not corporate, not monetized, and very deliberately not public.
🏷 Private forum + project brief — consistent independent interviews; no public dump exists.
“It was a brand stunt.” — no sponsor trail; no product reveal.
Cicada’s ethos showed up in tiny frictions: sign your messages; resist the urge to screenshot and boast; do the work. If you shared too much, later posters warned, the door closed.
When the medium becomes the message (2013)
⏱ Timeline callout — January 2013
The “clue” is a bootable ISO. Boot it and it prints primes, stalls at meaningful timestamps, and ships a guitar piece called 761.mp3 — The Instar Emergence.
By 2013, form did as much work as content. The ISO acted like a rite: you had to burn it, boot it, hear it. The track’s filename mirrors its duration in reverse (761 ↔ 167 seconds) — both primes — a wink that number theory still sits under the floorboards. Pick at the audio and you don’t get satanic whispers; you get a small poem about shedding your shell. Sometimes the point is to not hide more.
[“Parable” — excerpt surfaced with 761.mp3]
“Like the instar tunneling to the surface, we must shed our own circumferences; find the divinity within and emerge.”A second track appeared later, Interconnectedness. Its metadata and structure teased arithmetic, but mostly it set mood: puzzle as mixtape.
The book (2014)
⏱ Timeline callout — January 2014
A third public run culminates in Liber Primus — “First Book” — pages of text in a custom 29‑rune alphabet called Gematria Primus. Parts are solved. A lot still aren’t.
Gematria Primus sounds occult until you actually work a page; then it feels like engineering. Twenty‑nine runes mapped to twenty‑nine letters, each rune assigned a consecutive prime. Typical moves on solved pages look like this:
Runes → numbers (using the prime mapping).
Arithmetic (often mod 29, sometimes reversals over the 29‑rune line).
Numbers → runes → letters back into plaintext.
When it clicks, English emerges in declarative stanzas — austere, aphoristic, occasionally grandiose. The unsolved sections are where entire sub‑communities spend their weekends: testing transpositions, hunting missing keys, arguing whether we’re blocked by a step that never made it into public hands.
🏷 Liber Primus exists; several pages solved.
Why so much remains unsolved — missing key material vs. uncracked method.
A miniature walkthrough (one pipeline)
To give the “feel,” here’s a compact, end‑to‑end example mirroring mechanics used on solved lines:
Take a short rune string.
Map each rune to its prime index (2, 3, 5, … 109).
Apply a running key (e.g., subtract 1 from each, then wrap mod 29).
Convert indices back to runes, then to letters using the consensus table.
You recover a short English imperative.
The point isn’t to brute‑force every page here; it’s to show why reading this book is also computing it.
Signal, denials, and the last word (2015–2017)
2015 brought silence in January and a teachable moment in July, when a separate group using “3301” claimed a high‑profile hack. Cicada surfaced only to deny involvement with a signed message.
🏷 If it isn’t signed by 7A35090F, it isn’t Cicada.
2016 delivered a single image on the long‑associated Twitter account. Inside: a good signature and a nudge back to the book — “Liber Primus is the way…”
2017 left the cleanest coda we could ask for:
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Beware false paths. Always verify PGP signature from 7A35090F.
3301
-----BEGIN PGP SIGNATURE-----
... (omitted)Short of the key itself landing in your inbox, that’s as definitive as internet mysteries get: a signature, a warning, an instruction. And then nothing.
🏷 Unsigned “new Cicada puzzles” are canon. — explicitly contradicted by the 2017 note.
Theories that survive contact with the evidence
Two simplifications tempt newcomers. The first: Cicada is an ARG with a missing reveal. The trouble is the lack of a brand, a sponsor, or a payoff that benefits anyone publicly. The second: state recruitment. Possible? Sure. Proven? No.
Our best model is mundane and powerful: Cicada behaved like a private filter. The rewards were off‑stage — a quiet, values‑aligned project for the small number of people who solved under pressure without chasing clout.
For comparison, the U.S. Navy ran a very public recruiting ARG in 2014 — complete with branding, social posts, and post‑mortems. Cicada never did any of that.
Detours, myths, and namesakes
Plague‑doctor video (11B‑X‑1371): eerie, internet‑native art; not Cicada. The creator later surfaced and proved authorship with a sequel.
Law‑enforcement rumor mills: regional bulletins occasionally labeled Cicada a “hacker group”; a signed denial followed. Treat as a clash of statements with no conclusive resolution.
Ransomware brand‑hijacks (recent years): new crews have adopted the “Cicada3301” name and logo. There’s zero linkage to the original puzzle collective beyond opportunistic branding.
The feeling we’re left with
Read widely and a common register appears: not paranoia — devotion. Journalists who tried and failed still wrote about the thrill. Solvers who “won” don’t sound like dupes or cultists; they sound like people asked to do hard, interesting work in a style that matched their principles. And the signature discipline — verify or ignore — might be the sharpest civic lesson of the post‑viral internet.
When the public part ended, the group left a final instruction: verify the signature, ignore the imitators, finish the book.
Side‑bar — How to verify a PGP signature (2‑minute clinic)
Import the public key (warnings about trust are normal if you haven’t built a web‑of‑trust):
gpg --keyserver hkps://keys.openpgp.org --recv-keys 7A35090FVerify a clear‑signed note you’ve saved as
note.asc:
gpg --verify note.ascIf something is encrypted and signed,
gpg --decryptboth decrypts and verifies the signature. Expect “good signature” from the Cicada key when testing known artifacts.
Side‑bar — What is OutGuess (and why did it matter)?
OutGuess hides data in the statistical slack of images (especially JPEGs). In 2012, it was the crowbar that popped the first door: feed the cicada JPEG in, get a PGP‑signed message out. That one move — a payload inside a picture — set the tone for how Cicada buried signal in everyday formats.
Side‑bar — Gematria Primus: pocket card
Alphabet: 29 runes; some map to digraphs (TH, NG).
Values: each rune = the next prime (2…109).
Moves seen in solutions: mod‑29 shifts; Atbash‑like reversals over the 29‑rune line; occasional running‑key streams.
Summary & conclusions — the Curiolog take
Cicada 3301 makes the rare promise of the early internet feel credible again: open doors, private rewards, and proof over vibes. Read across the artifacts, interviews, and signed messages and a simple shape emerges — not a brand and not (provably) a state actor, but a small, privacy-minded collective running a high-signal talent filter.
The public trail ends where the private work would reasonably begin: finish the book; verify the signature.
What’s solid [🟢 Verified]
2012–2014 public runs: image → phone → primes → domain → global posters; later ISO, music, and Tor stages.
PGP authenticity anchored to key 7A35090F; 2016 tweet and 2017 coda are signed and canonical.
Liber Primus exists; several pages are decrypted using consistent rune→number→mod-29 mechanics.
What’s likely [🟠 Plausible]
Recruitment/filter for a values-aligned, privacy/crypto project (fits tasks, tone, and inside accounts).
Discouraging public collaboration was intentional: to surface disciplined, low-ego solvers.
What we reject or leave unproven [🔴/🟠]
Unsigned puzzles and late “comebacks” presented as canon — reject unless signed by 7A35090F.
Government/agency affiliation — unproven. Possible in theory, unsupported in evidence.
Viral-marketing/brand stunt — no sponsor trail, no product reveal; doesn’t fit how the campaign operated.
Why it matters now
A living case study in verification literacy (PGP or it didn’t happen) in an age of copycats and deepfakes.
A rare, global hybrid puzzle that stitched street posters to Tor onions, OS images, audio, and runes.
A reminder that some of the internet’s best work resists spectacle: slow, quiet, and receipt-driven.
What would change our mind
A new signed message from the Cicada key (with fresh, reproducible artifacts) altering the record.
A credible leaker providing primary assets + signatures that withstand independent verification.
A cryptanalytic breakthrough that unlocks blocked Liber Primus sections and reveals new keys.
If you’re new here, start with the PGP clinic and the first OutGuess extraction. If you’re an old hand, consider writing a reproducible pipeline for one solved page of Liber Primus — so the next wave spends time thinking, not rebuilding the toolkit.
Sources
Primary artifacts & technical
Boxentriq — Cicada 3301: An Internet Mystery (First Puzzle Walkthrough): https://www.boxentriq.com/code-breaking/cicada-3301
iBotPeaches (GitHub) — cicada_3301 repo (keys, messages, Liber Primus scans): https://github.com/iBotPeaches/DeconstructingCicada
Uncovering Cicada Wiki — Liber Primus, Gematria Primus, 2016/2017 messages archive: https://uncovering-cicada.fandom.com/
Internet Archive — “761.mp3 — The Instar Emergence” & “Interconnectedness”: https://archive.org/ (search: “Cicada 3301 761.mp3” / “Interconnectedness 3301”)
PGP key reference — Cicada public key (ID 7A35090F) via keys.openpgp.org: https://keys.openpgp.org/
Reporting & first-person accounts
The Guardian (Alex Hern), 2014 — overview and attempt: https://www.theguardian.com/
The Telegraph, 2013–2014 — news coverage & poster sightings: https://www.telegraph.co.uk/
The Independent (James Vincent), 2014 — explainer: https://www.independent.co.uk/
Fast Company (Michael Grothaus), 2014 — Joel Eriksson interview & “Inside the 3301 cabal”: https://www.fastcompany.com/
Rolling Stone (David Kushner), 2015 — Marcus Wanner profile: https://www.rollingstone.com/
Business Insider, 2016 — report on the signed Twitter image: https://www.businessinsider.com/
Audio / video explainers
LEMMiNO — Cicada 3301: An Internet Mystery (YouTube documentary): https://www.youtube.com/
Great Big Story — 2-part mini-doc on Cicada 3301: https://www.youtube.com/
WNYC / New Tech City (2013) — “Meet the Teenage Codebreaker…”: https://www.wnycstudios.org/
Community hubs & living archives
Reddit — r/cicada: https://www.reddit.com/r/cicada/
(Optional) r/UnresolvedMysteries megathreads (contextual discussion): https://www.reddit.com/r/UnresolvedMysteries/
Comparative case study (recruitment ARGs)
U.S. Navy — Project Architeuthis (official write-ups / coverage): https://www.navy.mil/ (search: “Project Architeuthis case study”)
Debunks, denials & name collisions
Planned Parenthood 2015 hack — news coverage + Cicada PGP-signed denial (archived): check major outlets + archive mirrors
“11B-X-1371” plague-doctor video — creator Parker Warner Wright’s claims & follow-up proof: interviews/social posts circa 2015–2016
Modern ransomware using “Cicada3301” name — threat intel (e.g., Truesec, Unit 42): vendor blogs / advisories